Maximizing Service Protection: The Ultimate Overview to Electronic Safety Solutions
In the fast-paced and ever-evolving landscape of company safety and security, the dependence on digital security services has come to be vital for safeguarding beneficial possessions, confidential information, and preserving operational connection. In this guide to digital protection options, we will certainly check out the latest fads, advanced innovations, and ideal practices to strengthen your organization against possible threats and susceptabilities.
Importance of Electronic Security Solutions
When thinking about the security of possessions and delicate details, the significance of digital safety and security solutions can not be overemphasized. In today's interconnected world, where cyber hazards are regularly developing and ending up being more sophisticated, organizations must focus on carrying out robust electronic safety and security actions to secure their information and procedures. Electronic protection remedies include a large range of modern technologies and practices developed to prevent unauthorized accessibility, information breaches, malware, and various other cyber threats.
One of the crucial advantages of electronic safety and security solutions is their capacity to give real-time tracking and risk detection. BQT Solutions. Through devices like intrusion detection systems, firewalls, and security information and event management (SIEM) systems, companies can proactively determine and react to safety and security incidents prior to they escalate right into major violations. Furthermore, electronic safety and security solutions help make sure compliance with industry regulations and standards, securing organizations from possible legal and monetary repercussions
Kinds of Electronic Safety Equipments
Given the essential value of electronic safety and security services in safeguarding services versus cyber dangers, it is vital to check out the different kinds of electronic protection systems readily available to improve defense and strength. Among the most usual types of digital security systems is the firewall, which acts as a barrier between a business's internal network and external networks, filtering system out potentially dangerous data. Intrusion Discovery Solution (IDS) are also critical, as they keep an eye on network traffic for dubious activity and alert administrators to potential hazards. In addition, companies typically rely on encryption technologies to safeguard delicate information both at rest and in transportation. Access control systems, consisting of biometric readers and keycard accessibility, help regulate entry to physical rooms and secure properties. Video security systems contribute in monitoring and recording tasks within and around the premises. By employing a mix of these electronic protection systems, companies can develop a durable protection versus various security risks.
Carrying Out Gain Access To Control Steps
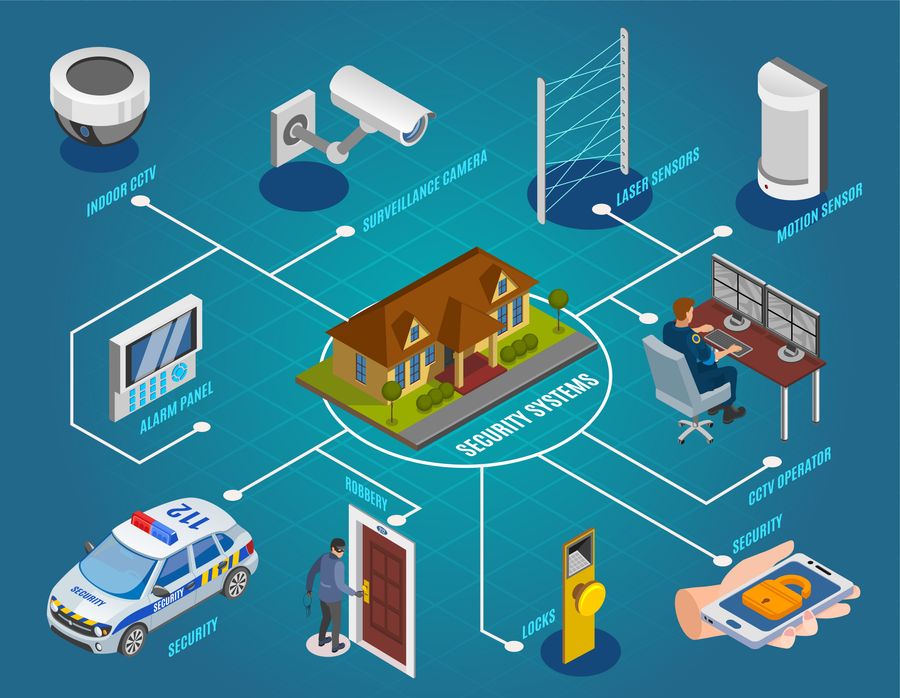
Additionally, access control measures can be integrated with monitoring systems to monitor and tape people' Recommended Reading motions within protected locations. This combination boosts security by giving an extensive summary of who is accessing certain locations at any kind of given time. Accessibility control systems can be configured to limit gain access to based on time, area, or private credentials, enabling organizations to tailor safety and security procedures according to their certain requirements.
Cybersecurity Best Practices
To enhance total protection stance, executing durable cybersecurity finest methods is important in protecting electronic assets and information honesty. Conducting routine safety and security audits and analyses assists recognize weaknesses and areas for enhancement.
Developing a detailed case reaction strategy allows swift and reliable responses to security breaches, decreasing prospective damages. Encrypting sensitive information both en route and at rest gives an additional barrier versus information violations. Implementing access controls based on the concept of least benefit limits the direct exposure of essential systems and info to only those that need it for their functions. Normal back-ups of data guarantee that in the occasion of a ransomware assault or information loss, important info can be recovered. Accepting a positive technique to cybersecurity through continuous monitoring and hazard knowledge helps find and alleviate potential dangers prior to they rise. By integrating these best practices into cybersecurity approaches, businesses can strengthen their defenses his explanation against progressing cyber dangers.
Monitoring and Monitoring Solutions

Video clip surveillance remedies provide remote monitoring capacities, enabling licensed workers to watch on the properties even when off-site. In addition, advanced features like activity discovery, facial acknowledgment, and license plate acknowledgment enhance the total safety stance of the organization. Integrating security systems with alarm systems and gain access to control better Click This Link strengthens the security infrastructure, allowing an aggressive feedback to prospective security breaches.
Final Thought
Finally, electronic safety and security solutions are crucial for taking full advantage of company security. By executing access control measures, cybersecurity finest methods, and monitoring and surveillance options, services can properly guard their properties and info. It is necessary to buy the appropriate electronic security systems to guarantee the safety and security and safety of the company. Keep in mind, avoidance is crucial in securing against possible dangers and susceptabilities (BQT Sideload locks).